Fun Tips About How To Get A Botnet
The more the bots, the bigger the botnet, and the more significant the impact.
How to get a botnet. The doj also used the moobot malware to copy and delete the botnet files and data, according to the doj, and then changed the routers' firewall rules to block remote management access. Get free botnet protection with avast one, which detects malware, viruses, and other threats in real time to protect you against incoming infections. Fake internet traffic generation ad fraud botnets can use your web browser to send traffic to online advertisements without your consent.
Learn what botnet stands for, what damage it can do & how to protect yourself. As opposed to “traditional” botnets that are formed of internet of things (iot) devices such as dvrs, cc cameras, or smoke detectors, mantis uses hijacked virtual machines and powerful servers. In botnet brute force attacks, the bots receive a list of websites (or ip addresses) and some pairs of usernames and passwords (generally less than three) from botmaster for each ip address.
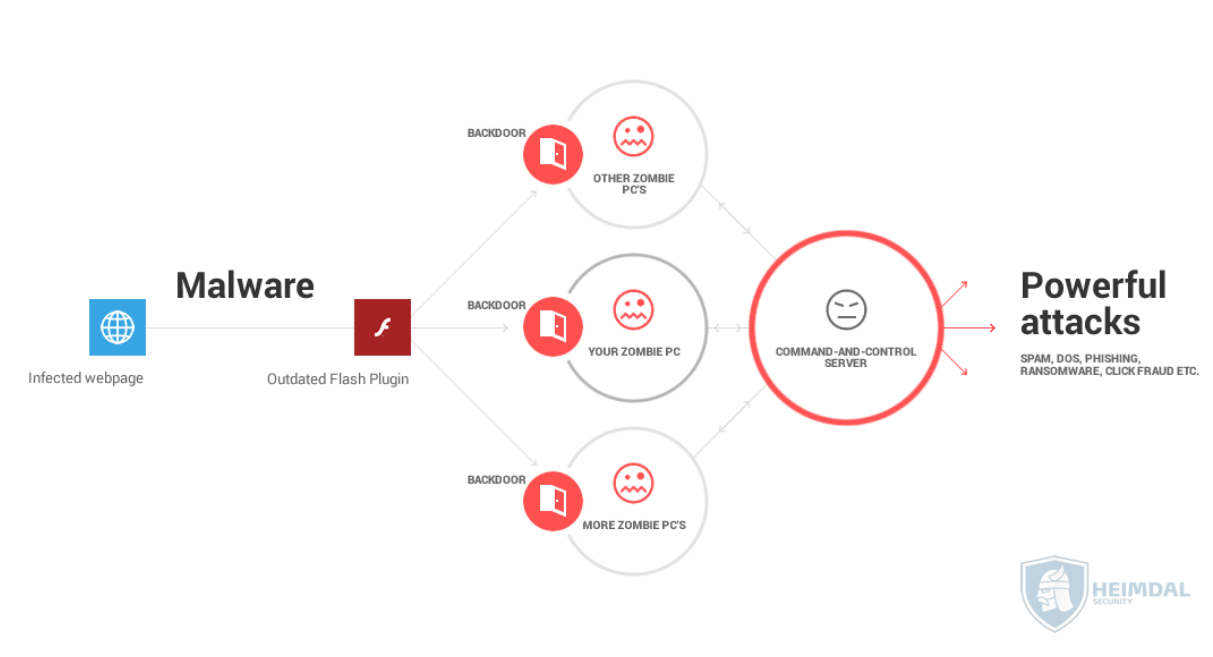
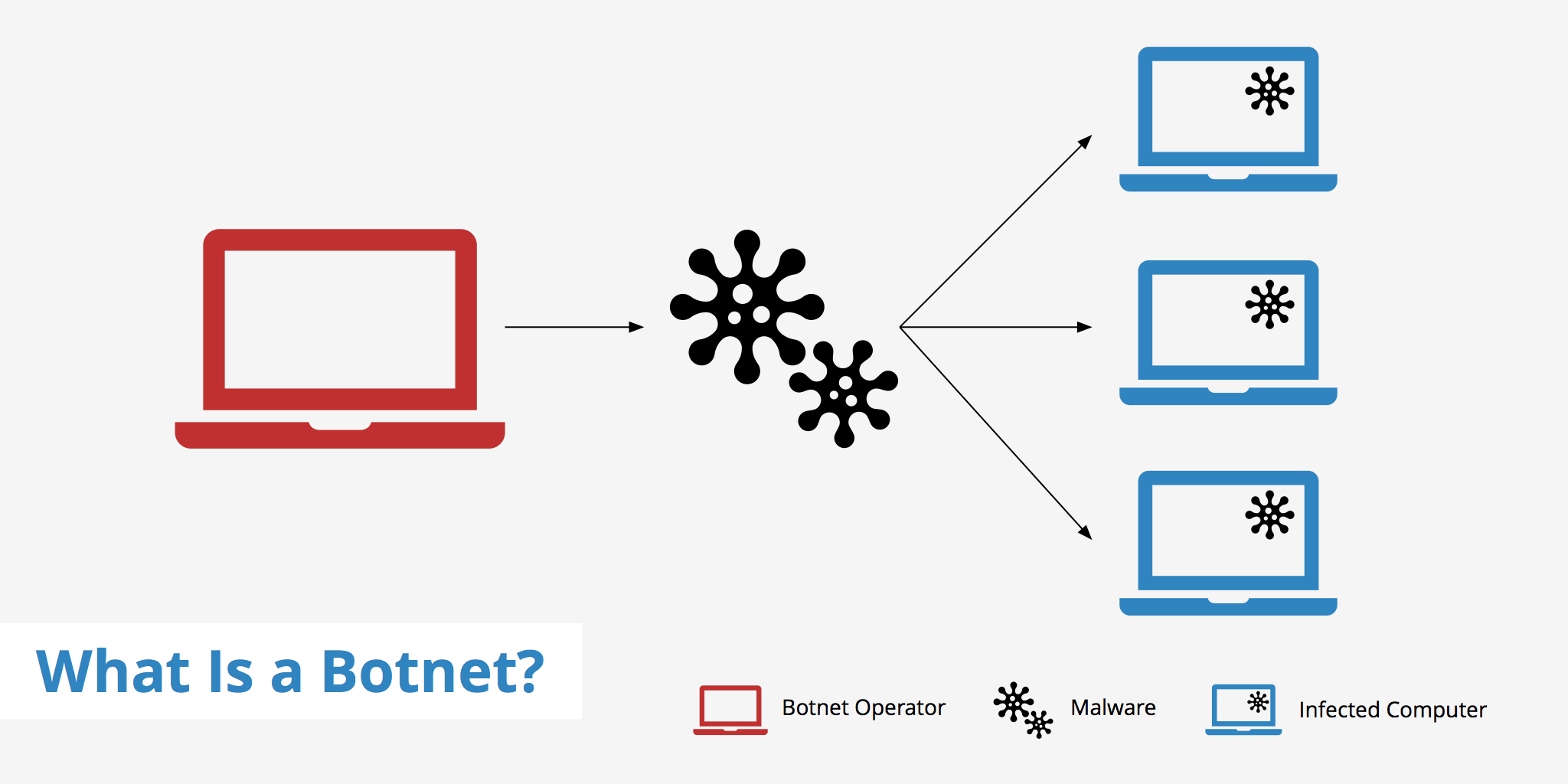
The process defrauds marketers by generating fake traffic and earning revenue. Once the botnet carrier enters your device, it would inform the botmaster, and the botmaster would take control of your system. Botnet word is evolve from word robot and network where the robot is infected by malware and then becomes part of any network.
The us government recently announced it disrupted a botnet allegedly belonging to russia’s gru. The stages of creating a botnet can be simplified into these steps: Promo protect all your devices, without slowing them down.
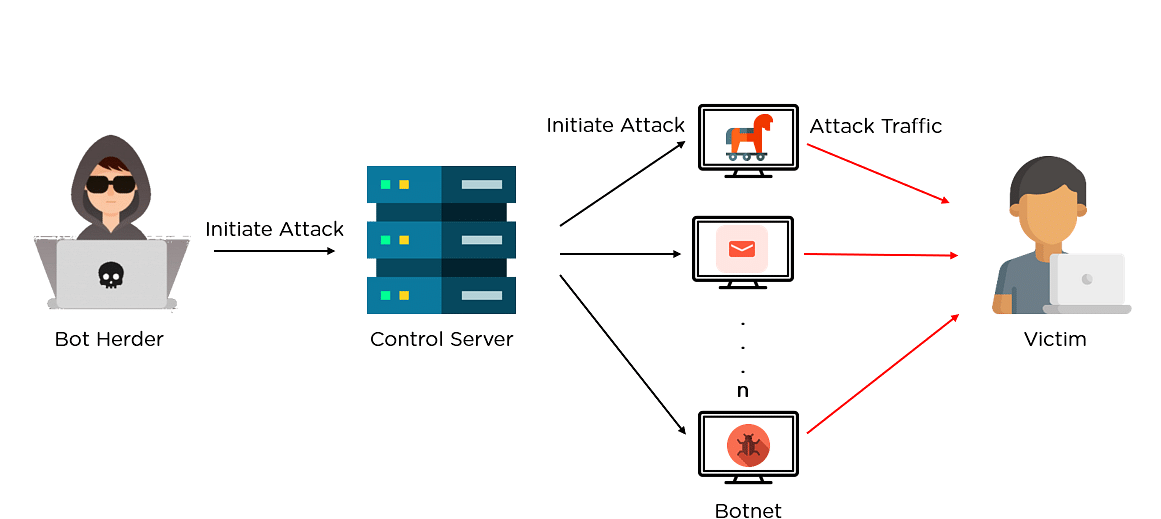
According to ethical hacking researcher of international institute of cyber security bots were in recent news for attacking financial sector in usa. A cybercriminal might send you an email that looks like it comes from your bank, cable provider, favorite streaming service, or credit card company. A bot herder intends for users to remain unaware of their exposure and eventual malware infection.
13k views 1 year ago. Scammers use different strategies when launching botnet attacks. You will have to change adapter settings and.
Such botnets are hard to notice because they use very few resources. This is a tutorial on how to build your own botnet using byob a great tool to build out botnets that allows you to edit payloads. If malicious code to recruit your computer into a botnet can get in, so can ransomware, financial malware, and other threats.
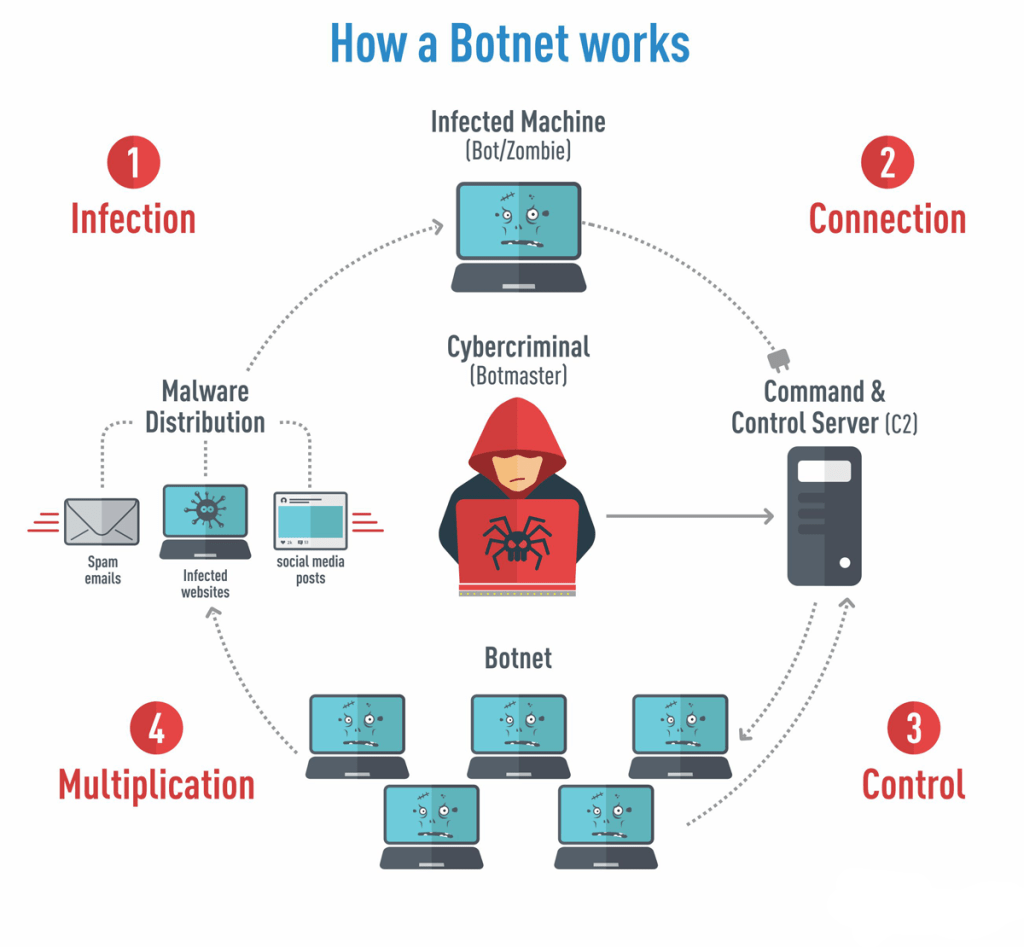
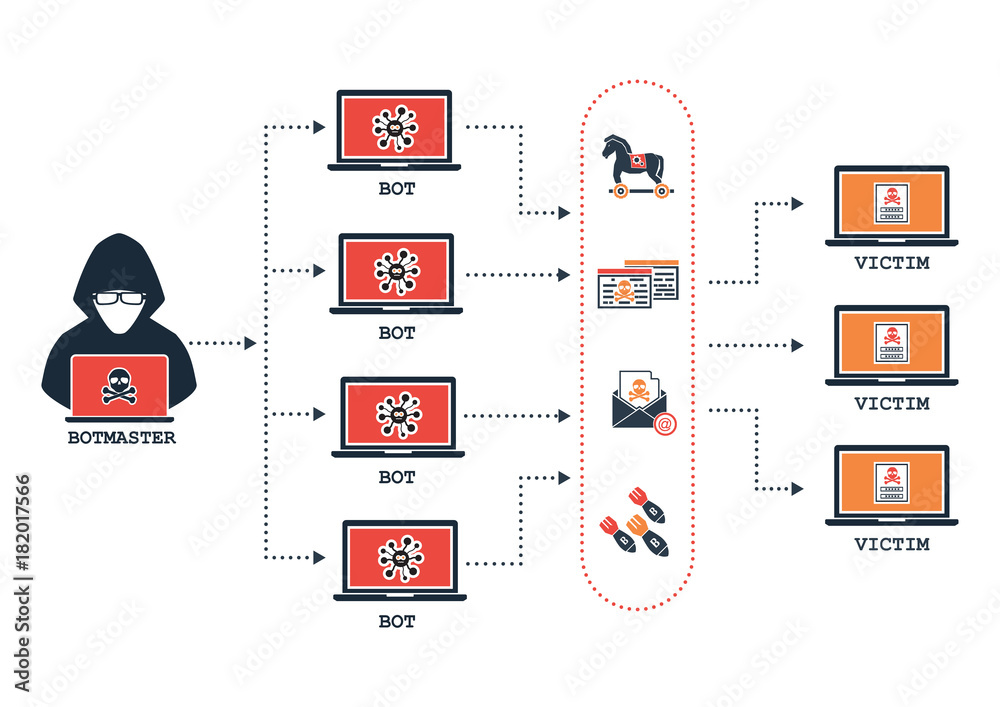
These are normally controlled without their legitimate owner’s knowledge, and they are often used to inflict harm as part of various malicious schemes. A botnet is a collection of internet connected devices (anything from pcs to iot devices) which are infected by the same malware. Using methods and tools that can be found online in minutes, a botnet creator can create a central command and control server and then use social engineering to inject malware onto the victim’s.
Expose infect and grow activate in stage 1, the hacker will find a vulnerability in either a website, application, or user behavior in order to expose users to malware. Prepping the botnet army: The first step in creating a botnet is to infect as many connected devices as possible, to ensure that there are enough bots to carry out the attack.
Such malware infections are usually. This tip discusses how to effectively use various botnet detection techniques and tools. This is a simple to use free tool that runs in docker and acts as a c2 server.

![What is a Attack? A Simple Definition [+How to Prevent]](https://gogetsecure.com/wp-content/uploads/2022/02/Botnet-Attack-Definition.jpg)